About identification management
Effective identification management helps organisations to reduce and/or prevent fraud, loss of privacy and identity theft by applying good practice processes.
The identification management elements
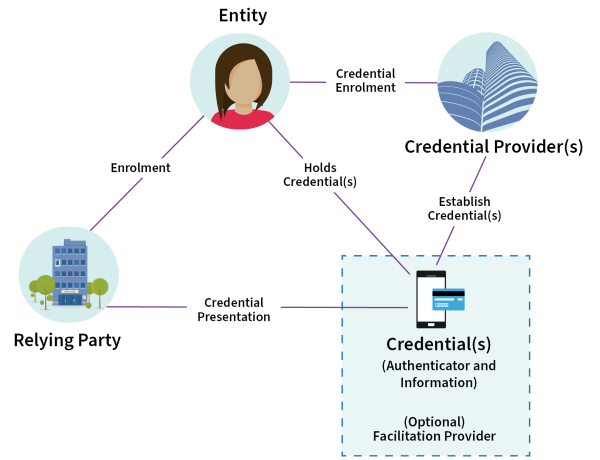
Detailed description of the image
This diagram depicts how the elements in identification management work together.
An Entity (for example, a person) wants to get a Credential that they can use to get a service from a Relying Party (for example, an organisation). The Entity goes to a Credential Provider to get an applicable Credential and then either presents their Credential directly to the Relying Party or the Credential Provider presents it to the Relying Party for them, sometimes via a third party.
Descriptions of the elements and their relationships
Relying party becoming a Credential Provider
A Relying Party (or organisation) can become a Credential Provider when they have completed an enrolment process and decide to establish a credential that will be relied upon by other Relying Parties in the future. For example, a passport, practicing licence, or staff access card.
Identification management and other practices
Identity management
Identity and identity management tend to focus on attributes and their management rather than the wider processes and human behaviours essential to prevent identity theft and the impacts of this. The material in this website takes a different approach to the area, to solve many of the problems that have been hampering effective development of solutions.
Privacy and security
Identification management is a practice that is separate from, but closely related to Privacy and Security. While several requirements within the Identification Standards contribute to information privacy and security, they do not replace the need to apply relevant standards within these separate practices.
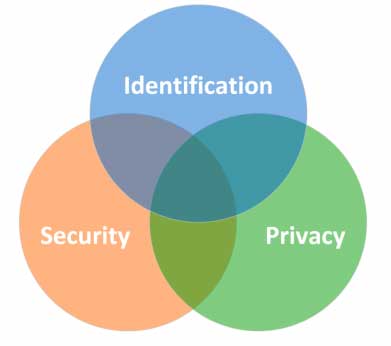
Detailed description of the image
Utility links and page information
Last updated

