Guide to optimising network traffic for cloud services
This guide describes how agencies can reduce remote workers’ dependence on their agency networks and improve performance by reconfiguring their VPN from forced tunnel to inverse split tunnel architecture.
Purpose
This document provides technical advice for agencies, security managers of information technology and network engineers managing network capacity for remote workers.
It’s intended for agencies that already have remote workers with VPN access from agency-managed devices who may be experiencing problems with reliability or performance when accessing cloud services.
Context
Agencies can experience performance and reliability issues that affect remote workers.
This can occur as a result of heavy use of cloud productivity applications being routed through an organisation’s corporate network by users connecting over the organisation’s VPN.
High-volume personal traffic, such as music or video streaming, can also create additional load on your network.
Requiring all network traffic from remote users to traverse your agency network also creates a single point of failure. This can block remote workers from accessing cloud applications that they could otherwise continue using.
Inverse split tunnelling
In most cases there is little security benefit from routing public cloud traffic through internal networks and proxies. VPNs can be configured to allow defined network traffic directly between user devices and approved cloud services without increasing risk to your information or organisation.
Examples of high traffic public cloud services that should be considered for inverse split tunnelling include:
- productivity applications — such as Microsoft Office 365, Microsoft Teams, Zoom and Skype for Business
- music or video streaming services — such as YouTube and Netflix.
Assumptions
This guide assumes that you already have:
- a functioning VPN capability
- secure end-user devices with a VPN client, host-based firewall and up-to-date anti-virus, and
- the ability to remotely manage end-user devices and push policy and configuration updates.
Optimising network traffic
VPN-forced tunnelling
The most common configuration of VPN deployments is forced tunnelling. This is where all network traffic from your end-user devices must route back to your agency network through the VPN. Connections to cloud services are then routed back to the internet.
This is often done in order to monitor and control network activity from the end-user device. This architecture is recommended for organisations that have not yet begun using cloud-based productivity or business applications. Where an organisation makes extensive use of cloud services this architecture can impose unnecessary reliability and performance degradation.
View larger image of the diagram (PNG 40KB)
Detailed description of the diagram
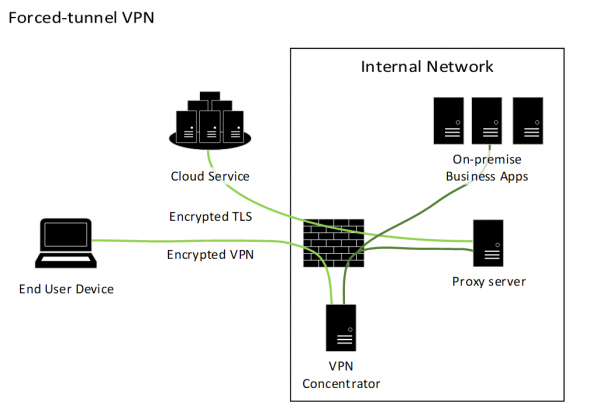
This diagram describes the flow of network connections in a forced-tunnel architecture.
On the left is a laptop representing an end-user device, and a cluster of computers representing a cloud service. The end-user device and cloud service are represented as being located on the internet.
On the right is a box representing the boundary of an agency internal network. This box contains a firewall, and computers representing a VPN concentrator, a proxy server and multiple on-premise business applications.
Lines are drawn representing a series of network connections. The first connection is from the end-user device, passing through the internet and agency firewall, terminating at the VPN concentrator. This line is labelled encrypted VPN.
Two unlabelled connections start at the VPN concentrator connecting to the proxy server and on-premise business applications. The last line, labelled Encrypted TLS, starts at the proxy server and passes through the firewall and across the internet to the cloud service.
This architecture has several limitations:
- Your organisation’s network becomes a point-of-failure for staff accessing cloud services. If there is an issue with internet access through your network, people working remotely will be unable to access cloud services.
- The bandwidth or packet-forwarding capacity of your organisation’s internet connection may cause performance issues.
- Remote users may find that some cloud services do not function correctly with traffic forced through a VPN.
Inverse split tunnelling
Inverse split tunnelling is a VPN configuration where network traffic from the end-user device to approved cloud services is allowed directly and does not traverse the VPN or your corporate network.
We do not recommend full split tunnelling. This allows all internet traffic to bypass the VPN and could allow an attacker on the internet to access your agency’s internal resources through the end-user device.
View larger image of the diagram (PNG 40KB)
Detailed description of the diagram
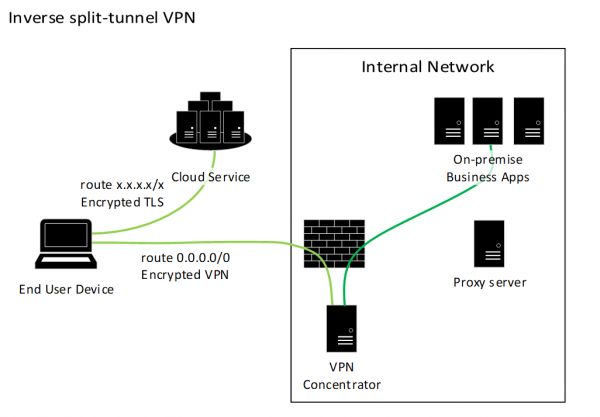
This diagram describes the flow of network connections in an inverse split tunnel architecture.
On the left is a laptop representing an end-user device, and a cluster of computers representing a cloud service. The end-user device and cloud service are represented as being located on the Internet.
On the right is a box representing the boundary of an agency internal network. This box contains a firewall, and computers representing a VPN concentrator, a proxy server and multiple on-premise business applications.
Lines are drawn representing a series of network connections. The first connection is from the end-user device, passing through the Internet and agency firewall, terminating at the VPN concentrator. This line is labelled encrypted VPN.
A second connection starts at the VPN concentrator and terminates at the On-premise Business Applications. A third and final connection, labelled Encrypted TLS, starts from the end-user device, connecting to the cloud service, passing only through the Internet cloud.
There are several aspects to inverse split tunnel configuration:
- Network routing tables
- VPN policy configuration
- Firewall configuration
- Type of network traffic
Depending on your VPN product you may need to configure any or all of these.
Split tunnelling definition and requirements — New Zealand Information Security Manual (NZISM)
Functionality that allows personnel to access both a public network and a VPN connection at the same time, such as an agency system and the internet.
The NZISM requires that split tunnelling must be disabled when using a VPN from a mobile device, including laptops and workstations used out of the office.
The rationale is that a split tunnel can allow access to an agency’s systems from another network. This risk is addressed by the use of the inverse split tunnel and strong end-user device controls including host-based firewalling.
Inverse split tunnel VPN — NZISM
View larger image of the diagram (PNG 47KB)
Detailed description of the diagram
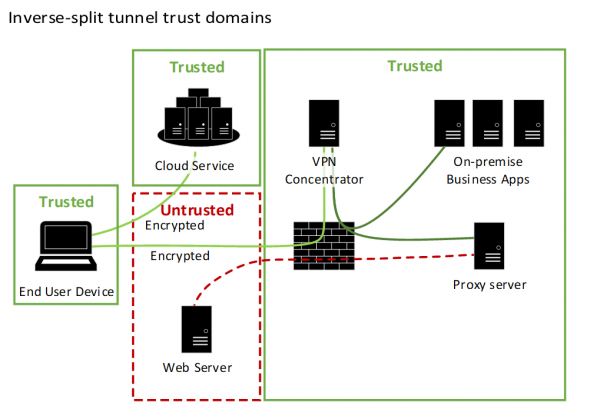
This diagram describes the trust domains of the inverse split-tunnel architecture.
There are 4 boxes, each representing a trust domain. Three of the boxes are labelled Trusted. These contain the end-user device, cloud service and the agency internal network. The fourth box is labelled Untrusted and represents the public Internet, containing a generic web server.
Two lines representing network connections are drawn from the end user device, 1 connecting to the Trusted Cloud Service and the other to the VPN concentrator inside the agency internal network. Both lines are labelled Encrypted.
Two connections are drawn from the VPN Concentrator to the Proxy server and On-premise Business Applications within the agency internal network. A final connection is drawn from the Proxy server to the generic Web Server in the Untrusted Internet domain.
Importantly, no connections are represented from the end user device directly to any device in the Untrusted domain.
In this architecture the end-user device only connects to trusted environments and does not connect to, nor accept connections from, devices on the untrusted public network.
See also:
- NZISM 21.1 Distributed working: Agency-owned mobile devices — Government Communications Security Bureau
- How-to guides for common VPN platforms — Microsoft
These guides can be used for any cloud service, not just Microsoft options.
Securing end-user devices
Host-based firewall
The VPN client or other host-based firewall on the end-user device must be configured to drop all connection attempts from the internet. If you have end-user devices that do need to accept connections from the internet, then the host-based firewall must be configured to only allow the minimum necessary access and to drop all other traffic.
See also:
- Virtual Private Networks (VPNs) — NCSC UK
- Alternative ways for security professionals and IT to achieve modern security controls in today's unique remote work scenarios
Securing access to cloud services
You may have configured the cloud services you use to only allow connections from your own networks. You’ll need to configure cloud services to accept access from any Internet Protocol (IP) address. To mitigate the risk of unauthorised parties gaining access to your information in the cloud we strongly recommend the following additional controls.
Single sign-on (SSO)
We strongly recommend that agencies which have an existing federated identity capability use this for managing users’ access to cloud applications. This ensures that the cloud service does not require separate management of user accounts, and may allow users to access cloud services without logging in if they have already logged in to the agency directory from their device.
Multiple factor authentication (MFA)
We strongly recommend configuring cloud services to require multiple factor authentication for all access. This reduces the likelihood of an attacker guessing or gaining access to your information in cloud services.
Logging and reporting
You’ll need to maintain visibility of who is accessing your information in the cloud. You should review access logs periodically and enable centralised logging where possible.
Configuring cloud services
Microsoft Office 365
SSO
If your agency is already using Office 365 it’s likely that single sign-on is already configured.
Configuring single sign-on varies depending on how your Office 365 deployment has been designed so we can’t provide guidance for this.
MFA
Guidance for configuring MFA for Microsoft Office 365.
Set up multi-factor authentication for Microsoft 365 — MicrosoftVPN configuration
Microsoft have provided guidance for configuring split tunnel access to Office 365 at the link below. They have also included step-by-step configuration guides from key VPN vendors.
How to quickly optimise Office 365 traffic for remote staff and reduce the load on your infrastructure — MicrosoftZoom
SSO
Zoom provides configuration guides for enabling SSO with a wide range of directory solutions including Azure Active Directory, ADFS, Okta and GSuite / Google Apps.
Zoom configuration guide for Single Sign-On
VPN configuration
Configure your VPN policy and routing to allow direct connections to the domains and IP addresses listed in Zoom network firewall or proxy server settings.
See also:
Software-as-a-Service security principles — NCSC UK
Last updated

