Binding Assurance Standard
This standard provides specific controls for ensuring an entity is appropriately bound to their entity information in order to prevent identity theft.
Application of this standard
This standard applies to any Relying Party (RP). The RP is accountable for the controls stated in this standard, even if they have employed or contracted aspects to other parties.
Application of the controls in this standard will contribute to the reduction of identity theft, entity information (account) takeover, and therefore the impacts that result.
Version and effective date
This standard is effective from 1 October 2024 and replaces the earlier version.
Version 2 (current version) — consolidates control BA3.03 and another control and establishes a separate objective to contain the counter fraud and investigation controls.
Version 1 (effective 1 March 2021) — first published version of the Standard.
Historic versions of the Identification Standards — Department of Internal Affairs
The Information Assurance Standard is an evolution of part of the Evidence of Identity (EOI) Standard Version 2.0 – December 2009, in particular the requirements outlined in Table 8 of the EOI Standard relating to Object C – Presenter ‘links’ to identity.
Evidence of Identity Standard (EOI) Standard version 2.0 — Department of Internal Affairs
Scope
This standard applies whenever an association is established between an Entity and Entity Information, whether during enrolment or a subsequent transaction.
Binding an Entity to Entity Information establishes that the Entity Information, regardless of its level of assurance, relates to the Entity claiming it. Effective binding ensures the authorised use of Entity Information needed for business operations.
Entity Binding can be undertaken at various times over the life of the Entity Information, not just at enrolment. For example:
- when the Entity information is orphaned — through loss of all Authenticators or where no Entity Binding occurred at enrolment (for example, registering of a birth, unassigned stored value card)
- adding new Authenticators
- increasing the assurance level in the binding processes
- when the Entity Information is believed to have been compromised.
The requirements in this standard are explicitly related to the binding of Entities to Entity Information and do not include considerations for general security, messaging methods, or implementation matters.
The binding of Entities to Entity Information, for which the Entity is not the subject, is covered in guidance.
Authority to act for another Entity
In relation to the scope of Identification management, this standard relates to the quality of the connections between Entities and Entity Information, as indicated in Diagram 1.
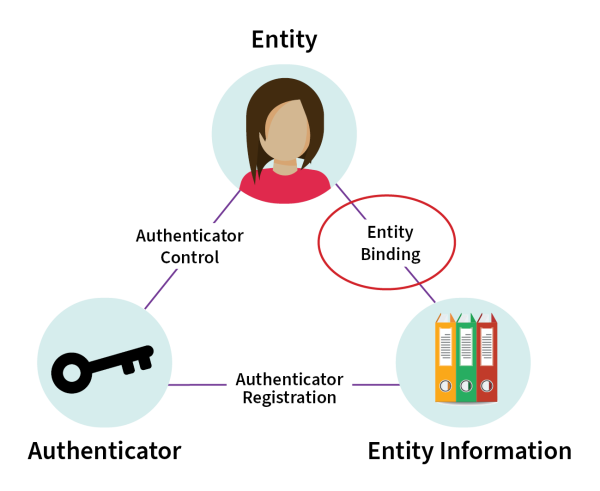
Detailed description of diagram
This diagram shows a triangle representing the connection between Entity (in this example, represented by a person) at the top of the triangle, Authenticator (represented by a key) at the bottom left, and Entity Information (represented by files of information) at the bottom right.
The connection between Entity and Entity Information is labelled Entity Binding. The connection between Entity Information and Authenticator is labelled Authenticator Registration. The connection between Authenticator and Entity is Authenticator Control.
There is a circle around the Entity Binding connection to indicate the primary process that is the scope of this standard in relation to the other elements.
Relationship with other identification standards
Table 1 describes each of the assurance components and the processes they relate to. This standard addresses the second of these assurance components — Binding Assurance.
| Assurance component | Description |
|---|---|
|
IA Information Assurance |
Robustness of the process to establish the quality and accuracy of Entity Information. |
|
BA Binding Assurance |
Robustness of the process to bind the Entity to Entity Information. |
|
AA Authentication Assurance |
Robustness of the process to ensure an Authenticator remains solely in control of its holder. |
|
FA Federation Assurance |
Additional steps undertaken to maintain the integrity, security and privacy of a credential used in multiple contexts. |
Before applying this standard
Enrolment is a broad process which includes (but is not limited to) the initial collection of Entity Information from an Entity, the creation or association of an Authenticator, if required, and the binding of these 3 elements. Enrolment could be carried out over several transactions.
The factors for binding are the same types as those used for authentication:
- something the entity knows (knowledge factor)
- something the entity has (possession factor)
- something the entity is or does (biometric factor).
During enrolment, the provision of Entity Information by the Entity establishes a minimum level of assurance while the transaction session is maintained. As soon as there is an interruption in the transaction there is the possibility that a returning Entity may not be the same Entity that initiated the enrolment.
Requirements for Entity Binding
Objective 1 — Binding risk is understood
Rationale
For entities to trust that their information and the services they are enrolled in are being adequately protected from unauthorised access and use, the binding level should be consistent with the risk posed.
Relying parties may also need to achieve specific levels of assurance to mitigate risks and potentially to comply with legislation.
BA1.01 Control
The RP MUST carry out an assessment of the binding risk posed by any service before offering it.
Additional information — While any risk assessment process can be used, specific guidance is available on assessing identification risk of which binding is a part.
Objective 2 — Entity can claim an instance of Entity Information
Rationale
Before binding an Entity to Entity Information, the relevant instance of Entity Information needs to be identified.
Entity Information is expected to be specific to a single Entity, therefore only 1 Entity can have a legitimate association or binding with an instance of Entity Information.
Failure to ensure Entity Information is specific to a single Entity can result in Entity Information being inadvertently disclosed or it being taken over by another Entity once binding occurs. If there are multiple claims to the same Entity Information, counter fraud investigation might be indicated.
BA2.01 Control
The RP MUST ensure the Entity provides enough information to identify a distinct instance of Entity Information.
BA2.02 Control
The RP MUST be able to identify when an instance of Entity Information has been claimed.
Additional information — Orphaned or unclaimed instances of Entity Information are at greater risk of being incorrectly bound to an Entity. A subsequent claim to an association with Entity Information, that has already been recorded as having been bound, should raise concerns.
Objective 3 — Entity is the subject of Entity Information
Rationale
Establishing that an Entity is the subject of either Entity Information they have provided or are claiming (for example, orphaned) is fundamental to preventing impersonation of an Entity for the purposes of gaining a benefit or avoiding an obligation.
BA3.01 Control
The RP MUST establish the level of binding assurance (BA) required, for establishing the relationship between the Entity and the information collected.
BA3.02 Control
The RP binds each piece of Entity information at the established level of binding assurance (BA) required, using the following binding factor types:
- knowledge factors that are not publicly known, easily determined or predictable
- possession factors that contain enough features to assess as genuine
- biometric factors with appropriate measures to detect spoofing attempts (for example, recordings, masks, makeup or prosthetics etc.)
For level 1 — This control does not apply, the Party relies on the ability of the Entity to identify a distinct instance of Entity Information.
For level 2 — The RP MUST use a minimum of 1 of the binding factor types or an existing Authenticator or Credential of equal or greater assurance level.
For level 3 — The RP MUST use a minimum of 2 of the binding factor types or an existing Authenticator or Credential of equal or greater assurance level.
For level 4 — The RP MUST use a biometric factor compliant with controls AA9.04, AA9.05 and AA10.01 with either of the knowledge or possession binding factor types; or an existing Authenticator or Credential of equal assurance level.
Additional information — The Authentication Assurance Standard can be used as additional guidance on desirable features for each of the factor types and their levels. An existing registered Authenticator, potentially for another delivery channel, can be used to support binding, as can Credentials.
BA3.03 Control
The RP MUST NOT assign a level of assurance to the binding, where an Authenticator or Credential is used, if the level has not been declared.
BA3.04 Control
The RP MUST limit the number of unsuccessful attempts to bind, disallow further attempts and trigger further investigation.
Objective 4 — Entity uniqueness in a context
Rationale
Having each instance of Entity Information distinguishable from another in a context and ensuring that each instance is claimed by 1 Entity still allows for 1 Entity to claim multiple instances of Entity Information.
In some contexts, there can be an additional need to ensure that an Entity has an association to 1 and only 1 instance of Entity Information. Otherwise known as Entity uniqueness. Examples can include contexts such as passports, justice or certain entitlements.
BA4.01 Control
The RP SHOULD ensure an Entity cannot claim more than 1 instance of Entity Information, where Entity uniqueness is required by the context.
Objective 5 — Entity Binding integrity is maintained
Rationale
The longer an Authenticator is used to represent the binding between an Entity and Entity Information, especially when challenged remotely, the more likely it can become compromised or the Entity can have lost control of it. In this case the Entity Binding has not being maintained.
Changes to the risk profile for the service or transaction, may necessitate increasing the binding which will retest it.
BA5.01 Control
The RP retests Entity Binding at least once every 5 years to ensure it remains consistent with the level of binding assurance (BA) required.
For levels 1 and 2 — The RP SHOULD undertake this control.
For levels 3 and 4 — The RP MUST carry out this control unless authentication events involve a biometric factor.
BA5.02 Control
The RP applies counter fraud techniques, where possible.
For levels 1 and 2 – The control does not apply
For level 3 – The RP SHOULD apply counter fraud techniques.
For level 4 – The RP MUST apply counter fraud techniques.
Additional information – More information is available in the guide Counter fraud techniques.
BA5.03 Control
The RP MUST store appropriate detail about the Entity binding process to enable queries or investigation in the future.
What compliance means
In order to comply with this standard ALL the controls will be met at the level required.
Voluntary compliance by any RP wishing to follow good practice for contributing to the prevention of identity theft and fraud, will be against the levels indicated by undertaking a risk assessment.
Compliance with this Standard given through means such as contractual requirements, cabinet mandate, legislation etc., will include mechanisms for assessment and certification. The RP will meet the levels determined by the risk assessment and any additional requirements specified.
Related advice
If the RP is providing binding assurance services to other parties, there will be additional controls to be applied in the Federation Assurance Standard.
For additional guidance on implementing the controls in this standard, refer to Implementing the Binding Assurance Standard.
Contact
Te Tari Taiwhenua Department of Internal Affairs
Email: identity@dia.govt.nz
Utility links and page information
Last updated

