Assessing identification risk
Understand how to conduct an identification risk assessment for your service or transaction. Use this to calculate the right strength of identification processes to protect against information fabrication and identity theft.
Understanding identification risk
Identification has 2 risks:
Risk 1 — incorrect information is provided for a service or transaction.
This is the risk of providing or denying a service or transaction to a person based on someone giving incorrect information during enrolment for or later use of a service or transaction.
Risk 2 — someone is incorrectly linked to or associated with the information and/or authenticator used in a service or transaction.
This is the risk that by using someone else’s information and/or authenticator, a person could gain an advantage they are not entitled to, avoid obligations (such as paying fines), or impact the entitlement of someone else.
Who engages in information fabrication or identity theft, and why
Considering the types of people who give incorrect information or carry out identity theft, and why they do this, helps in assessing identification risk.
Table 1 gives a list of the 4 main motives behind giving incorrect information and identity theft, and the types of people who do this.
Table 1: Main motives for identify theft
| Motive |
Motive description |
Parties |
|
Gain
|
To get access to money, goods, services or information |
People who understand the value of the service or transaction (for example, other customers or scammers) |
|
Misrepresentation
|
To use someone else’s identification information and associated things like qualifications and reputation
to carry out an activity a person would not otherwise be able to do
or
to avoid obligations that are associated with their own information
|
People with a particular agenda (for example, competitors, egotists, cheats, criminals, terrorists) |
|
Personal attack
|
To cause someone financial loss, damage to reputation, physical or emotional harm, or embarrassment |
People with a grudge against someone (for example, ex-partners, colleagues, competitors)
People with a grudge against the service provider (for example, competitors, former employees)
|
|
Nuisance
|
To have fun or do something because of feeling bored. This motive is less likely to target a specific person
and does not carry an intention to harm someone |
People with no particular agenda |
Establishing if there is identification risk
To check if identification risk exists in a situation, ask these 5 questions:
- Can anyone receive money or incur a cost through using the service (for example, a benefit, a grant or a debt)?
- Can anyone receive other benefits through using the service (for example, a product, training or access)?
- Is information about an entity being collected and stored by the service?
- Can the service result in the release of their personal or sensitive information?
- Can the service result in a document or data source being issued (for example, a licence or a digital ID) that could subsequently be used as a form of evidence of identitification, qualification or reputation?
If you answer ‘Yes’ to any of these questions, then you should undertake a full identification risk assessment.
Situations that are not identification risks
- Internal fraud — when staff deliberately undermine the system and its processes.
- Collusion — when a person deliberately gives away their information or access.
- System attacks — when skilled people circumvent a (computer) system’s security to access networks and records (this usually involves information about multiple individuals).
- Information loss — when identifying information has been lost (accidentally or otherwise) but is not used for fraudulent purposes.
You will need other strategies in place to deal with the risks associated with these activities.
Transactions that have no identification risk
- Giving non-sensitive information — Example: giving someone an application form.
- Giving non-sensitive advice — Example: giving someone information on how to access services and transactions.
- Collecting a payment — Example: collecting a parking fine.
Conducting an identification risk assessment
To establish which identification processes to put in place to protect your service or transaction, and to determine the ideal assurance level or strength of these processes, you first need to conduct an identification risk assessment.
An identification risk assessment is part of wider risk management and should be conducted alongside Privacy and Security assessments. Even if you’ve already built risk management into your service, effective identification management needs a more detailed understanding of the scope of your service and of each of the transactions within it.
To conduct an identification risk assessment, you need to understand the:
- information the service collects and uses
- consequences of an event happening
- impact levels for each consequence
- controls that are in place to prevent or reduce a consequence, and how strong they are
- level of likelihood that a consequence will occur, given the controls in place
- the resulting level of identification risk for a service or transaction.
Categories of identification risk consequences
Depending on the service or transaction, the consequences of incorrect information or identity theft fall into 1 or more of the following categories:
- Financial loss or liability — for example, a person uses stolen or fictitious information to receive a financial benefit they are not entitled to and causes a direct financial loss to the source of the funds.
- Unauthorised release of sensitive information — for example, a person releases someone else’s personal information to an unauthorised party.
- Qualification, identification or reputation loss or damage — for example, a person uses a stolen qualification, identification or reputation which results in them representing themselves as falsely having certain skills or characteristics. If they use it to fraudulently receive services, this causes an organisation to lose credibility with the public.
- Other loss or liability — for example:
- the service provider is in breach of legislation or policy
- a person is prevented from gaining medical treatment, undertaking training or accessing a facility
- a person avoids obligations.
Assessing the consequences and impact level of each category
For each risk and its category(s), consider:
- the information that can be viewed and updated in the service, especially where it’s relied on for decision making
- which affected party/parties will be impacted
- how each party will be impacted (for example, monetary amounts, type of information, regulatory compliance, nature of inconvenience, media coverage, degree of reputational damage) to put a value on or to describe the nature of the impact.
Next, think about the severity within each category if the consequence were to happen, and assign 1 of the following impact levels to each:
- Minimal
- Minor
- Moderate
- Significant
- Severe
To do this, use your own risk framework to describe what each of the levels means and select an appropriate impact level for each category of consequences.
Impacts that should not be considered
Take care not to assign any consequences to events that happen indirectly as a result of incorrect information or identity theft, as this will overly exaggerate the impact levels you assign a service or transaction.
This is particularly true if the consequences flow on to events that may be related to but do not concern the service or transaction.
Examples
- As the result of a transaction, a driver licence is issued to someone other than the entitled person.
A consequence of this transaction might be that the licence is used as identification to receive a benefit elsewhere.
However, as the initial intent of the licence is not to provide verification of someone’s identifying information but rather to certify that the person is authorised to drive, the impact of using the licence to receive a benefit elsewhere is not an identification risk of the actual transaction (to get a driver licence); it’s an identification risk of the other organisation's process.
- As the result of a transaction, an unauthorised party gets access to someone’s sensitive information. Consequences of this transaction might be:
-
- the unauthorised party uses the information to blackmail the person or to find them and cause them bodily harm
- the unauthorised party publishes the information causing distress to the person. Because of other people reading the information, the person is dismissed from their job.
The distress the person feels is a consequence of this transaction. However, the person losing their job is not a consequence of the transaction; it’s a consequence of the employer’s use of the disclosed information.
Identifying controls and assessing their effectiveness
After you’ve assessed the possible consequences of an event happening, and the impact levels these could have, identify the controls that are in place and assess how effective these controls are.
Controls are only effective if they are applied consistently across all the steps of a service or transaction. If a control can only be applied to 1 or some steps of the service or transaction, you’ll need to assess each step separately.
Tools for assessing identification risk
There are 4 types of controls.
Preventative — Stop the event or the consequence from happening.
Corrective or Reductive — Do not stop an event or a consequence from happening but reduce the degree of impact.
Detective — Identify events so you can put corrective measures in place to prevent these from happening in the future.
Directive or Disincentive — Implement rules, policies or training, or assess the value of the service as being of too little consequence to make it a target.
What is not counted as a control
The strengths of the identification processes are determined later so the following processes are not counted as controls:
- identification processes for when someone is requesting a service or completing a transaction
- authentication processes for when someone returns to a service or to complete a transaction.
Once you’ve determined which controls are in place for each risk, establish the degree to which each control is applied (its effectiveness), in other words, how often or how comprehensively it’s applied.
Assessing the likelihood of a consequence occurring
For each risk and its consequence categories, assess all the controls that are in place and then assess the likelihood that the consequences could still occur.
Note: You can only assess the likelihood of a consequence occurring once you’ve chosen what controls to put in place for it.
The levels of likelihood are:
- Rare — robust controls are in place that prevent or remove the impact of a consequence in all but the most exceptional circumstances.
- Unlikely — many controls are in place with some minor ineffectiveness that may allow a consequence to occur in limited circumstances.
- Possible — several controls are in place with such ineffectiveness that a consequence should occur in some circumstances.
- Likely — minimal controls are in place and/or controls lack effectiveness such that it’s highly probable a consequence will occur.
- Almost certain — there are no effective controls in place to prevent a consequence from occurring.
Help with assessing the level of likelihood
Sometimes it may be difficult to accurately establish the likelihood of a consequence occurring. The following methods may help:
- Check other services offered by the organisation with similar identification risk exposures.
- Check other organisations’ services with similar identification risk exposures.
- Read relevant published data on the likelihood of a particular identification consequence occurring for particular service types.
- Get specialist and expert advice.
Never assume it will not happen just because it hasn’t happened yet.
Plotting the level of risk
Plot the impact and likelihood for each risk and consequence category using a matrix such as in Figure 1. This results in 1 of 25 possible outcomes or levels for that risk. In general, the highest number associated with each risk represents the remaining identification risk level for that risk.
Figure 1: Risk matrix
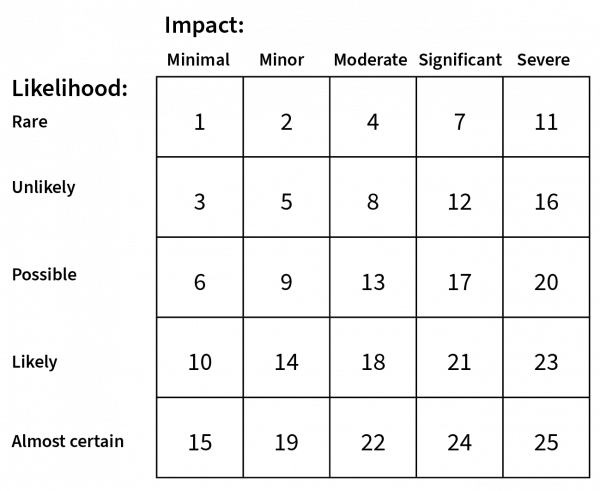
Using level of risk to calculate strength of identification processes
You can then convert the 2 levels of remaining identification risk for a service or transaction into a value that represents the strength (or assurance level) of the identification processes needed to reduce the adverse effects of this risk.
That is, the greater the level of identification risk for a transaction, the stronger (more comprehensive and stringent) your identification processes need to be, as shown in table 2.
Table 2: Level of risk to strength of identification process
| Plotted level for Risk 1 |
Plotted level for Risk 2 |
Strength of identification process |
| 1–3 |
1–3 |
Negligible — Level 1 |
| 4-6 |
4-10 |
Low — Level 2 |
| 7-19 |
11-19 |
Moderate — Level 3 |
| 20-25 |
20-25 |
High – Level 4 |
There are 3 risk identification processes and they match the risks in the following way:
- Verify the accuracy of information — Risk 1
- Bind an entity to information and/or an authenticator — Risk 2
- Ensure an authenticator is still being used by its owner — Risk 2
Applying risk treatment
Risk treatment is a process of managing a risk for a service or transaction by choosing and implementing options to change the consequences that could happen or the likelihood of them happening.
Risk treatment options
Risk treatment options for identification risk are:
- avoid the consequences of risk entirely by deciding not to start or continue the activity that gives rise to the risk
- modify 1 or more controls
Note:
Modifying controls may alter the level of risk and therefore the strength of the identification processes. If this happens, it’s important to reassess the risks, consequences, controls and likelihood to make sure the identification processes are at the right level.
- modify the strength (assurance level) of identification processes
- share or transfer the consequence liability to another party (not recommended as accountability for the risk remains and the transfer will often not hold)
- retain the risk of consequences occurring by formally accepting them.
Choosing the appropriate risk treatment options
Choosing the appropriate risk treatment options involves balancing the cost and effort of implementation against the benefits.
A variety of risk treatment options can be implemented either individually or in combination with each other.
Responsibility for implemented risk treatment options
It’s important to identify and agree on an appropriate person to be responsible for and maintain the risk treatments that have been implemented for a service or transaction. This person must have the authority and ability to:
- get resources to effectively manage the risk treatment
- change the design of the service
- be accountable for the decision regarding the appropriate identification management assurance levels for each identification process.
- accept the untreated risk associated with the service.
Monitoring and reviewing identification risk
It’s important to consistently monitor and review the identification risks for your service or transaction as part of the wider risk management programme. This includes reviewing:
- how the service or transaction operates to check whether the controls and risk treatments are performing appropriately
- the identification risk assessment and identification processes to make sure they still align with current standards and best practice.
Tools for assessing identification risk
The Department of Internal Affairs has developed some workbooks to help with completing identification risk assessments.
The Service Assessment Workbook assesses the overarching service and focuses on Risk 1.
The Transaction Assessment Workbook is used for each transaction within a service and focuses on Risk 2. To make it easier to assess a large volume of transactions, a summary form of assessment can be done using the Bulk Transaction Workbook.
Advice or help — contact the Identification Team
Identification Team
Te Tari Taiwhenua Department of Internal Affairs
Email: identity@dia.govt.nz
Utility links and page information


