Federation Assurance Standard
This standard provides additional controls for parties that provide credentials and/or presentation facilitation mechanisms on which others rely.
Application of this standard
This standard applies to any Credential Provider (CP) and any Facilitation Provider (FP) that facilitates the presentation of 1 or more Credentials. The CPs and FPs are accountable for controls stated in this standard, even if they have employed or contracted aspects to other parties.
Application of the controls in this standard will contribute to the reduction of identity theft, entitlement fraud, misrepresentation of abilities and the impacts that result.
The scope of the requirements in this standard is explicitly related to the identification aspects of federated credentials. It does not include considerations for security, other implementation matters or any contractual agreements.
Version and effective date
This standard is effective from and replaces all earlier versions.
Version 3 (current version) — minor clarifications and control refinement.
Version 2 (effective ) — separates the role of Facilitation Provider from Credential Provider and refines wording of some controls such as correlation and use of unique identifiers.
Version 1 (effective ) — first published version of the Standard.
Historic versions of the Identification Standards — Department of Internal Affairs
Scope
This standard applies whenever an individual, organisation or group wants to establish a Credential that can be reused by Entities in identification processes with multiple Relying Parties (RP). It also applies to individuals, organisations or groups that create mechanisms that facilitate the presentation of 1 or more Credentials. This includes where a Credential Provider takes an active part in facilitating the presentation of their own Credential(s).
To enable Credentials to be reliably used in this way requires the development of some common agreements, which is why these Credentials are referred to as federated credentials. The standard does not cover the nature of these agreements but provides identification requirements for service providers wishing to become Credential Providers or Facilitation Providers.
In relation to the scope of Identification management, this standard relates to Credentials and the roles that establish, manage and facilitate their presentation to a Relying Party.
For more information, see About identification management.
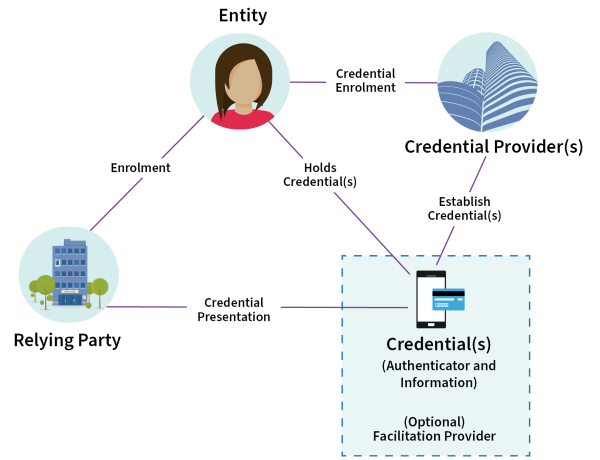
Read the detailed description of diagram
This diagram depicts the roles, artefacts, relationships and processes that ensures there are controls for parties that provide credentials on which others rely.
- Roles
- Entity: An example of an Entity is a person. An Entity enrols with a Credential Provider to get 1 or more Credentials.
- Credential Provider(s): A Credential Provider is a party that provides an Entity with 1 or more Credentials that meet appropriate identification requirements.
- Relying Party: A Relying Party provides a service to an Entity and may need Credentials to establish certain information that will enable the provision of that service.
- Facilitation Provider: A Facilitation Provider is a party that facilitates the presentation of 1 or more Credentials to a Relying Party.
- Artefacts
- Credentials: A Credential contains information and an Authenticator that has been bound to an Entity.
- Processes
- Enrolment: When an Entity enrols with a Relying Party to get a service.
- Credential Enrolment: A specific instance of Enrolment when an Entity enrols with a Credential Provider to get 1 or more Credentials.
- Establish Credential(s): When a Credential Provider establishes 1 or more Credentials for an Entity.
- Facilitation Provider: A Facilitation Provider is a party that facilitates the presentation of 1 or more Credentials to a Relying Party.
- Holds Credential(s): When an Entity is bound by an Authenticator to 1 or more Credentials.
- Credential Presentation: When a Credential held by an Entity is presented to a Relying Party as evidence. This may be done directly or facilitated by a Facilitation Provider.
Relationship with other identification standards
Assurance components
Table 1 describes each of the assurance components and the processes they relate to. A separate standard has been developed for each component.
This standard addresses the last of these assurance components — Federation Assurance.
| Assurance component | Description |
|---|---|
|
IA Information Assurance |
Robustness of the process to establish the quality and accuracy of Entity Information. |
|
BA Binding Assurance |
Robustness of the process to bind the Entity to Entity Information. |
|
AA Authentication Assurance |
Robustness of the process to ensure an Authenticator remains solely in control of its holder. |
|
FA Federation Assurance |
Additional steps undertaken to maintain the integrity, security and privacy of 1 or more credentials, and their use in many contexts. |
Before applying this standard
Credentials
In this standard Credentials contain and make use of 3 aspects of information:
- Credential subject information — this is information that the holder of the Credential, is overtly aware of making available to a Relying Party for their decision making.
- Presentation information — this is information (including metadata) and associated processes that support the trust and operation of the Credential (for example, document security features, encryption, certificates).
- Facilitation information — this is information (including metadata) that is made available when the Credential Provider is involved in facilitating the presentation of the Credential to the Relying Party (for example, references, timestamps, transaction identifiers, logs).
At a minimum, a Credential consists of an Authenticator and Integrity mechanisms. Most Credentials have additional Presentation information that determines its use for specific purposes. For example, to travel or to drive.
A Credential ‘holder’ refers to the individual Entity with whom a Credential was first established — the rightful holder.
A Credential Provider refers to the party accountable for the establishment of a Credential and its availability for presentation.
Credential presentation
As Credentials evolve, they are likely to contain larger amounts of Credential subject information that can be made available to Relying Parties. This reflects the need to better serve the individual Entities that hold them, especially as we move to more digital and remote service delivery.
To maintain the privacy of the holder, not all the Credential subject information in a Credential needs to be made available to a Relying Party. There are 2 forms of limitation:
- Partial presentation — a subset of the Credential subject information is made available to the Relying Party
- Derived value presentation — 1 or more of the values in the presentation are deduced or inferred from the value in the Credential. For example, age can be inferred from a date of birth.
Credentials can be presented in a manner that is either facilitated (for example, using a digital service to provide Credential subject information to an RP) or non-facilitated (for example, presenting a document directly to an RP). In a non-facilitated presentation, there is no involvement of a party other than the Entity and the Relying Party.
Providing and facilitating the presentation of a Credential can involve 1 or more parties working together. Other standards and jurisdictions segment these using terms such as Information Provider, Attribute Provider, Credential Service Provider, Verifier and so on. Regardless of the number of parties that are working together, the Facilitation Provider is the accountable party for the purposes of assurance.
Note: A Credential Provider facilitating the presentation of their own Credential is also a Facilitation Provider.
Facilitation
Facilitation involves the establishment and use of a mechanism that can facilitate the presentation of 1 or more Credentials (fully or partially) in response to a request from a Relying Party.
These mechanisms include exchanges, hubs (for example, RealMe®) and digital wallets.
A mechanism ‘holder’ refers to the individual Entity with whom the mechanism was first established — the rightful holder.
A Facilitation Provider refers to the party accountable for the establishment and use of a facilitation mechanism.
Document structure
This standard divides requirements into 3 parts:
- Part 1 — Requirements for Credential Providers establishing Credentials.
- Part 2 — Requirements for Facilitation Providers establishing facilitation mechanisms.
- Part 3 — Requirements for the presentation of Credentials by Facilitation Providers.
Assumptions
The following assumptions have been made:
- Presentation of a Credential does not necessarily require the involvement (facilitation) of the Credential Provider.
- There are many ways in which a Credential can be presented, including physically or digitally and whether all or only part of the Credential subject information is made available.
Part 1 — Requirements for Credential Providers establishing Credentials
The requirements in this section apply to the relationship between an Entity, a Credential Provider and the Credential that they establish.
The Credential Provider will apply the Information Assurance, Binding Assurance and Authentication Assurance Standards, as would a Relying Party during the Credential Enrolment process.
Objective 1 — Credential risk is understood
Rationale
For holders to trust their Credential is being adequately protected from unauthorised access and use, the risk the Credential poses when used in multiple contexts needs to be understood by the Credential Provider and mitigated.
Obtaining and using a Credential has the potential to expose holders to additional risks arising from increased collection of information.
As Credentials move from narrow purposes with minimal attributes to ones that can fulfil several identification requirements, care needs to be taken with the accumulation of information. This includes the attributes that are contained in the Credential regardless of any limitation made during presentation.
Credential Providers may also need to achieve specific levels of assurance determined by contracts and/or legislation.
FA1.01 Control
The CP MUST carry out an assessment of the risk posed by the existence of the Credential before offering it.
Additional information – While any risk assessment process can be used, specific guidance is available on assessing identification risk.
FA1.02 Control
The CP MUST evaluate the risk of all information available to a holder viewing or managing their Credential and apply the corresponding level of authentication.
Additional information — Where credentials can be presented in privacy-preserving ways using partial presentation and derived values, the authentication level for presentation may be lower than that needed for Credential management.
Objective 2 — Credentials have recognised levels of assurance
Rationale
Consistent approaches to Credential establishment and an ability for Relying Parties to know the Credential and the Credential Provider are genuine, reduce the likelihood Credentials will be able to be used as avenues for identity theft and fraud.
As more Credentials become able to be used for multiple purposes, Entities can also use assurance levels to select Credentials best suited to the identification needs of the services they most commonly use.
FA2.01 Control
The CP MUST establish the Credential using identification processes that comply with the latest versions of the following standards:
Additional information — When a Credential Provider is enrolling an Entity and applying these standards, they do so in the role of a Relying Party. They become a Credential Provider at the point they establish the Credential for that Entity. The level to which assurance has been gained against the above standards will determine the levels to be declared in FA10.01.
FA2.02 Control
The CP MUST make level/s of assurance for the Credential subject information available to Holders, Relying Parties and Facilitation Providers.
FA2.03 Control
The CP MUST provide mechanisms, consistent with the intended assurance levels, that enable the Credential to be recognised as bona fide.
FA2.04 Control
The CP MUST provide mechanisms, consistent with the intended assurance levels, that enable the Credential Provider to be recognised as bona fide.
Objective 3 — Credential is privacy-preserving
Rationale
Using a Credential in multiple contexts offers numerous benefits to Entities. However, obtaining and using a Credential this way also has the potential to expose Entities to privacy risks arising from the capability to track and profile.
The availability of correlated volumes of data makes it vulnerable to uses that may not be anticipated or desired by the holder. These unexpected uses could inhibit adoption of federated services.
FA3.01 Control
The CP MUST reduce the ability for Relying Parties to correlate holders by not including the holder’s unique Entity Information identifier as part of a Credential.
Additional information — A unique Entity Information identifier is an identifier assigned by a context that uniquely identifies the set of Entity Information before a Credential has been established.
There are a few large organisations within New Zealand where their Entity Information identifier is also a public identifier for use in a specified purpose. Where these organisations become Credential Providers, they are unlikely to be able to comply with this control.
Therefore, consideration needs to be given to ensuring use of those Credentials are limited to the specified purpose for which the Entity Information identifier created.
FA3.02 Control
The CP MUST support minimisation of information by enabling the use of partial sets of Credential subject information, when possible.
Additional information — Credentials offered digitally can be more flexible. It is possible that when a Credential is connected to a facilitation mechanism, the Credential Provider could supply only some of the attributes contained in the Credential subject Information.
Objective 4 — Participation is inclusive
Rationale
Each Credential will have a purpose and corresponding holders who need them. Credential Providers have obligations including responsibilities under the Treaty of Waitangi and digital inclusion to ensure that Entities can participate on an equal footing. Therefore, consideration of the population of Entities who will depend on the Credential is essential so as not to contribute to the exclusion of participation by any group.
FA4.01 Control
The CP MUST identify the population of Entities who will require the Credential.
FA4.02 Control
The CP MUST support any Entity within the identified population to become a Credential holder.
Objective 5 — Credential is maintained
Rationale
Once a Credential is established there are several activities that maintain its relevance and integrity.
Some of these activities relate to managing the life cycle of the Credential such as updating, suspending and revoking the Credential.
Other activities enable fraud detection, for example, if interactions with Credentials are not logged and monitored, Credential Providers will not be able to appropriately prevent or investigate any misuse or compromise.
FA5.01 Control
The CP MUST provide the means for the Credential subject information contained in the Credential to be updated, by either:
- enabling Credential subject information in the Credential to be changed, or
- replacing the Credential, or
- establishing synchronous links to maintained sources of Credential subject information.
FA5.02 Control
The CP MUST provide the means for the holder to cancel a Credential.
FA5.03 Control
The CP MUST provide the means for the holder to report the loss or compromise of a Credential and receive support.
FA5.04 Control
The CP MUST provide the means for addressing holder complaints or problems arising from Credential establishment and maintenance.
FA5.05 Control
The CP MUST provide the means for addressing holder and Relying Party complaints or problems arising from non-facilitated Credential presentation.
FA5.06 Control
The CP MUST be able to update the Credential status to prevent its use, even if the responses to authentication challenges are successful, and can either:
- suspend the Credential, allowing for recovery in the future, or
- revoke, permanently disable or delete the Credential.
Additional information — If the holder has requested deletion of a Credential, consider suspending it for a period of 1 month before revoking to allow for recovery if needed.
FA5.07 Control
The CP MUST set an expiry on a Credential where the usage and risk indicates this to be appropriate.
FA5.08 Control
The CP MUST log all activity within the system, including but not limited to:
- who did the action
- when the action occurred
- what the action was — create, read, update or delete
- what was changed by the action — before and after.
Additional information — For physical Credentials this activity is more likely to apply to any database that supports it than the Credential itself.
FA5.09 Control
The CP MUST support additional confidence in the integrity of the Credential by taking preventative measures including but not limited to:
- auditing logs
- monitoring activities for adverse behaviours
- undertaking counter fraud measures.
Additional information — Refer to guidance on counter fraud measures.
FA5.10 Control
The CP MUST provide notifications to the holder that allow them to self-detect potential compromise, these can include but are not limited to:
- the last time the holder accessed their Credential (where applicable)
- any change made to the holder’s Credential.
Additional information — If the change is to contact information, notification needs to be sent to the contact information prior to the change or to an alternative contact.
Part 2 — Requirements for Facilitation Providers establishing facilitation mechanisms
The requirements in this section apply to the establishment of facilitation mechanisms.
Establishment of a mechanism includes confirming the relationship between the Entity and their Credentials and any new Authenticators associated with the mechanism.
Use of a facilitation mechanism to present Credential(s) is covered in the Requirements for presentation of Credentials by Facilitation Providers.
Objective 6 — Facilitation mechanism risk is understood
Rationale
For holders to trust facilitation mechanisms, they need to be sure that when they use a facilitation mechanism to present their Credentials, it is being adequately protected from unauthorised access and use. This is especially so when multiple Credentials can be linked through a single facilitation mechanism.
As increasing numbers of Credentials can be linked, care needs to be taken with the accumulation of information. This includes the attributes that are accessible by the facilitation mechanism regardless of any limitation made during presentation.
Facilitation Providers may also need to achieve specific levels of assurance determined by contracts and/or legislation.
FA6.01 Control
The FP MUST carry out an assessment of the risk posed by the facilitation mechanism, before offering it.
Additional information — While any risk assessment process can be used, specific guidance is available on assessing identification risk.
FA6.02 Control
The FP MUST evaluate the risk of all information available to a holder, viewing or managing their facilitation mechanism, and apply a corresponding level of assurance for authentication that complies with the latest version of the Authentication Assurance Standard.
Objective 7 — Binding assurance is maintained
Rationale
For Relying Parties and holders to trust a Facilitation Provider and their mechanisms, there needs to be certainty that there has not been a reduction in the binding assurance levels of the individual Credentials when they are connected. Certain conditions need to be met when Credential(s) are connected by a facilitation mechanism.
FA7.01 Control
The FP MUST provide 1 or more Authenticators for the facilitation mechanism.
Additional information — If a Credential Provider is facilitating presentation of their own Credential, this can be the same Authenticator as is used for that Credential.
FA7.02 Control
The FP MUST ensure the Authenticator has an equivalent level of assurance to the Authenticators of the Credentials being connected to it, using identification processes that comply with the latest versions of the following standard.
Authentication Assurance Standard
Additional information — If a Credential Provider is facilitating presentation of their own Credential, this can be the same Authenticator as is used for that Credential.
FA7.03 Control
The FP MUST ensure that the Entity proves control of the Authenticator for any given Credential before it is connected to a facilitation mechanism.
Objective 8 — Facilitation mechanism is privacy-preserving
Rationale
A holder using a facilitation mechanism potentially enables the building of profiles and tracking of the holder’s transactions. The availability of such data makes it vulnerable to uses that may not be anticipated or desired by the holder and could inhibit adoption of federated services.
Where a facilitation mechanism is used to connect multiple Credentials there is an increased potential to expose Entities to privacy risks arising from the expanded volume of available attributes.
FA8.01 Control
The FP MUST ensure the holder has given permission to make each Credential available to the facilitation mechanism.
FA8.02 Control
The FP MUST enable the holder to select which Credential subject information is added to the facilitation mechanism, where the Credential Provider allows for partial Credentials.
FA8.03 Control
The FP MUST inform the holder of any correlation or analysis of the use of their facilitation mechanism or the Credentials connected to it, undertaken for the purposes of detecting fraud or misuse.
FA8.04 Control
The FP MUST, except for the purpose given in FA8.03, only correlate or analyse a holder’s use of their facilitation mechanism or the Credentials connected to it, with the permission of the holder.
Additional information — It is expected that Facilitation Providers will at a minimum correlate or analyse this information for the purposes of detecting fraud or misuse. However, any other services offered to Entities or Relying Parties that also involve the use of this information, require the knowledge and choice of the holder.
Objective 9 — Facilitation mechanism is maintained
Rationale
Once a facilitation mechanism is established there are several activities that maintain its relevance and integrity.
FA9.01 Control
The FP MUST provide the means for the holder to add or remove any partial or full Credentials from a facilitation mechanism.
FA9.02 Control
The FP MUST provide the means for the holder to cancel a facilitation mechanism.
FA9.03 Control
The FP MUST provide the means for the holder to report the loss or compromise of a facilitation mechanism and receive support.
FA9.04 Control
The FP MUST provide the means for addressing holder complaints or problems arising from facilitation mechanism establishment and maintenance.
FA9.05 Control
The FP MUST log all activity within the system, including but not limited to:
- who did the action
- when the action occurred
- what the action was — gave permission, created, read, updated or deleted
- what was changed by the action — before and after.
FA9.06 Control
The FP MUST support additional confidence in the integrity of the facilitation mechanism by taking preventative measures including but not limited to:
- auditing logs
- monitoring activities for adverse behaviours
- undertaking counter fraud measures.
Additional information — Refer to guidance on counter fraud measures.
FA9.07 Control
The FP MUST provide notifications to the holder that allow them to self-detect potential compromise, including but not limited to:
- the last time the holder accessed their facilitation mechanism (where applicable)
- any change made to the holder’s facilitation mechanism.
Additional information — If the change is to contact information, notification needs to be sent to the contact information prior to the change or to an alternative contact.
Part 3 — Requirements for the presentation of Credentials by Facilitation Providers
The requirements in this section apply to the facilitated presentation of 1 or more Credentials or parts of Credentials to a Relying Party. This includes CPs who are facilitating the presentation of their own Credential(s).
Objective 10 — Presentations are consistent and recognised
Rationale
For Relying Parties to trust the integrity of information from Credentials they need to know they have been established and presented in a consistent and recognised way.
This includes knowing the Credentials are genuine and the levels of assurance they provide.
FA10.01 Control
The FP MUST make level(s) of assurance for the Credential subject information available to the Relying Party.
Additional information — Level of assurance is an expression representing the assurance level achieved by each of the 3 elements — information, binding and authentication. There can be a separate expression for each attribute in the Credential subject information.
FA10.02 Control
The FP MUST declare the lowest assurance level, where the presentation is not able to express individual levels of assurance.
FA10.03 Control
The FP MUST make the following additional Presentation information available to a Relying Party, where the presentation allows:
- Transaction identifier: A unique identifier for the presentation
- Issuance: A timestamp indicating when the Credential was established (updated)
- Expiration: A timestamp indicating when the Credential is expected to expire
- Credential validity: Information and/or mechanisms for determining the validity of Credentials, including if they have been revoked.
- Audience identifier: An identifier for the Relying Party that requested the presentation.
Additional information — Some Presentation information applies to the whole presentation, some to each value in the presentation.
Objective 11 — Presentations are privacy-preserving
Rationale
The presentation of Credential(s) should not expose any holder to a reduction in privacy. Active application of privacy principles such as data minimisation and providing permission contribute to good identification management practice and reduce identity theft and its impacts.
FA11.01 Control
The FP MUST ensure the holder has given permission to make Credential subject information available to the Relying Party.
FA11.02 Control
The FP MUST enable the holder to remove Credential subject information from the presentation, where the facilitation mechanism allows.
FA11.03 Control
The FP MUST only make available the Credential subject information that has been requested by the Relying Party.
Additional information — The Relying Party can request derived, inferred or estimated values from the Credential subject information, in which case the Credential Provider does not make available the full value.
FA11.04 Control
The FP SHOULD NOT make available Credential subject information to a Relying Party that cannot provide a purpose for collecting it.
FA11.05 Control
The FP MUST only release Presentation information and Facilitation information that are applicable to the Credential subject information the holder has given permission to be made available.
FA11.06 Control
The FP MUST reduce the ability for Relying Parties to correlate holders by not making available the same persistent identifiers in Credential subject information, Presentation information or Facilitation information, to multiple Relying Parties, except where allowed for by law.
Additional information — Providing each Relying Party with different identifiers for the holder prevents correlation between Relying Parties but will still allow a single Relying Party to track the activity of 1 holder within its context.
FA11.07 Control
The FP MUST, in response to a request for an anonymous presentation by a Relying Party, preserve the anonymity of the holder by not making available any persistent identifiers.
FA11.08 Control
The FP MUST take measures to ensure the information made available is not observed or disclosed to an unauthorised entity during presentation.
Objective 12 — Presentation content is unaltered
Rationale
Once a Credential holder has given permission for the Credential subject information to be made available to a Relying Party, they both need to be able to trust that the same information is received by the Relying Party.
FA12.01 Control
The FP MUST take measures to ensure the information made available during presentation is not altered.
FA12.02 Control
The FP MUST establish secure communication channels between all parties, where more than 1 party is required to complete a process.
Additional information — This refers only to where multiple parties are delivering the presentation of Credentials, not to the Entity or the Relying Party.
Objective 13 — Presentation can be investigated
Rationale
An important element of trust in any identification process is the ability for an Entity or Relying Party to question a process or presentation. While various controls allow for anonymity, pseudonymity and blinding of various parties in the Credential presentation process, none of these should prevent the investigation of a suspicious transaction.
FA13.01 Control
The FP MUST make available contact information to holders and Relying Parties, for the purposes of initiating a query about the presentation.
FA13.02 Control
The FP MUST collect the following information, where the presentation allows:
- Transaction identifier: A unique identifier for the presentation event
- Timestamp: A timestamp of when the presentation occurred
- Holder identifier: An identifier for the Entity that the presentation is about
- Audience identifier: An identifier for the Relying Party intended to receive the presentation
- Credential subject information: Values and references that describe the Credential subject information that was presented
- Credential Provider identifier: An identifier for the member of a multi-party Credential Provider who is the accountable party
- Presentation Information: Information about the integrity mechanisms used
- Facilitation information: Values and references that describe the facilitation information that was exchanged.
What compliance means
To comply with this standard, ALL the relevant controls will be met.
Voluntary compliance by any Party wishing to follow good practice for contributing to the prevention of identity theft and fraud, will be by self-assessment.
Compliance with this Standard that is given through such means as contractual requirements, Cabinet mandate, legislation and so on, will include mechanisms for assessment and certification.
Exemptions
Currently no process exists by which a mandated organisation can secure an exemption from the requirement to meet this Standard.
Related advice
For additional guidance on implementing the controls in this standard, refer to Implementing the Federation Assurance Standard.
Contact
Te Tari Taiwhenua Department of Internal Affairs
Email: identity@dia.govt.nz
Utility links and page information
Last updated

