Authentication Assurance Standard
This standard provides the controls used to ensure that 1 or more authenticators are still possessed and solely controlled by the authorised holder.
Application of this standard
This standard applies to any Relying Party (RP). The RP is accountable for the controls stated in this standard, even if they have employed or contracted aspects to other parties.
Application of the controls in this standard will contribute to the reduction of identity fraud by reducing the ability for unauthorised entities to gain access to the information and entitlements belonging to an enrolled entity.
The scope of the requirements in this standard is explicitly related to the use of authenticators and the process of authentication. It does not include considerations for security, messaging methods, or other implementation matters.
Effective date
This standard is effective from 1 March 2021.
It replaces the:
- Authentication Key Strengths Standard, Version 1.0 (published June 2006) and subsequent amendments
- Password Standard, Version 1.0 (published June 2006) and subsequent amendments, for organisations not subject to compliance with the New Zealand Information Security Manual.
Scope
This standard applies whenever a RP needs to ascertain that the current request is being made by the original entity — in other words, that the returning entity is the same entity that was initially enrolled.
Steps to detect unauthorised authentication events using analytics and behaviour measures that are not part of an Authenticator, are outside the scope of this standard.
In relation to the scope of Identification management, this standard relates to the strength of the authenticator, as indicated in diagram 1.
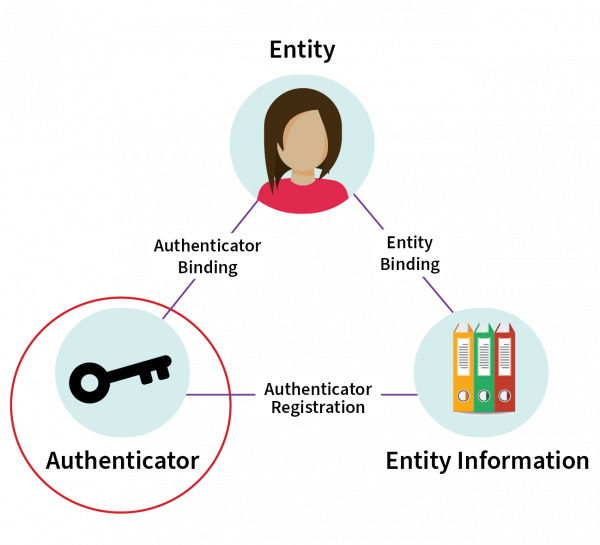
Detailed description of diagram
This diagram shows a triangle representing the connection between Entity (in this example, represented by a person) at the top of the triangle, Authenticator (represented by a key) at the bottom left, and Entity Information (represented by files of information) at the bottom right.
The connection between Entity and Entity Information is labelled Entity Binding. The connection between Entity Information and Authenticator is labelled Authenticator Registration. The connection between Authenticator and Entity is Authenticator Binding.
There is a red circle around Authenticator to indicate the scope of the content of this standard in relation to the other elements.
Relationship with other identification standards
Assurance components
Table 1 describes each of the assurance components and the processes they relate to. This standard addresses the third of these assurance components — Authentication Assurance.
| Assurance component | Description |
|---|---|
|
IA Information Assurance |
Robustness of the process to establish the quality and accuracy of Entity Information. |
|
BA Binding Assurance |
Robustness of the process to bind the Entity to Entity Information and/or Entity to Authenticator. |
|
AA Authentication Assurance |
Robustness of the process to ensure an Authenticator remains solely in control of its holder. |
|
FA Federation Assurance |
Additional steps undertaken to maintain the integrity, security and privacy of a credential used in multiple contexts. |
Before applying this standard
Authenticator types
Interpretation of this standard assumes a strong understanding of the 3 authentication factor types:
- something the authenticator holder knows — knowledge factor
- something the authenticator holder has — possession factor
- something the authenticator holder is or does — biometric factor
along with good knowledge about the characteristics of the entities to whom the service or transaction has been offered. See guidance in Authenticator Types.
Some articles discuss including somewhere the authenticator holder is — location factor — as a separate factor. Currently there is insufficient reason to support this being recognised as separate from something the authentication holder has. ‘Authenticator holder’ refers to the entity to which the authenticator was first bound, the rightful holder.
For implementations that utilise a third party as an authentication provider, this standard needs to be read in conjunction with the Federation Assurance Standard (under development).
The forthcoming guide to Implementing Authentication Assurance groups single factor authenticators and two-factor combinations into categories to provide an easy selection guide of known authenticators against required levels of authentication assurance.
Assumptions
The following assumptions have been applied for the development of this authentication assurance standard.
- For practical purposes, an authenticator will normally be paired with an identifier that enables look-up of corresponding entity information. This standard assumes an authentication challenge will be a one-to-one comparison (not one-to-many).
- Combining 2 or more authentication factors of the same type can add some additional strength in mitigating a threat but does not reduce the overall risk. The authentication assurance strength is determined by the best instance of the authentication factor type.
- Authentication combining 3 different authentication factors is possible, but the extra effort does not significantly improve on the strength obtained by the 2 strongest factors.
Requirements
Objective 1 — Authentication risk is understood
Rationale
For entities to trust that their information is being adequately protected from unauthorised access and use, the authentication level should be consistent with the risk posed.
Relying parties may also need to achieve specific levels of assurance to mitigate risks and potentially to comply with legislation.
AA1.01 Control
The RP MUST carry out an assessment of the authentication risk posed by any service before offering it.
Additional information — While any risk assessment process can be used, specific guidance is available on Assessing identification risk, of which authentication is a part.
Objective 2 — Ensure correct authenticator holder behaviour
Rationale
Under normal conditions most authenticator holders will act appropriately, and directive controls can be relatively effective. Penalties can also discourage incorrect behaviour.
However, authenticator holders might not initially be aware of their obligations, so these need to be communicated. Over time, understanding may diminish, and ongoing reminders may be appropriate.
At the higher levels of assurance, two-factor authentication helps enforce correct behaviour, so too does detecting behaviour that is not normal in the authentication process.
The RP needs to support correct behaviour by providing the means for the authenticator holder to report loss or compromise of an authenticator and appropriately manage the loss of control.
AA2.01 Control
The RP issues terms and conditions describing the authenticator holder’s obligations, including:
- the authenticator is for the sole use of the authenticator holder
- explaining how the holder will keep the authenticator safe
- that the holder reports loss of the authenticator including unauthorised use, sharing, theft of the authenticator, possible compromise, or any other suspected loss of control of the authenticator.
For level 1 — The RP SHOULD undertake this control.
For level 2 and above — The RP MUST undertake this control.
Additional information — Examples of expected behaviours:
- an access card should not be shared with another employee
- a passport should remain in the traveller’s possession
- or a device provided by the authenticator holder (such as a mobile phone) can only be used as an authenticator when it’s individually possessed and used by the holder.
AA2.02 Control
The RP provides regular communication to authenticator holders reminding them about their obligations, including:
- the authenticator is for the sole use of the holder
- the holder will keep the authenticator safe
- that the holder reports loss of the authenticator including unauthorised use, sharing, theft of the authenticator, possible compromise, or any other suspected loss of control of the authenticator.
For level 1 — This control is optional.
For level 2 and above — The RP MUST undertake this control.
AA2.03 Control
The RP limits the ability to share an authenticator by implementing 2 different factor types.
For levels 1 and 2 — This control does not apply.
For level 3 — The RP MUST undertake this control.
For level 4 — The RP MUST undertake this control using a biometric factor as 1 of the factors.
AA2.04 Control
The RP allows no more than 30 consecutive unsuccessful attempts to authenticate by any factor, disables the account and triggers further investigation.
For level 1 and 2 — This control does not apply.
For level 3 — The RP SHOULD apply this control.
For level 4 — The RP MUST apply this control.
Additional information — This control limits the total attempts by an attacker for any single challenge or combination of challenges of more than 1 authentication factor type. This upper limit applies to prevent multiple attempts that are only partially mitigated by subsequent controls such as the 30-minute timeout after a maximum of 5 incorrect attempts.
Where appropriate to the implementation, the RP MAY allow up to 3 re-entries for the same challenge attempt, for example the same received code for the code receiver method.
AA2.05 Control
The RP MUST provide the means for the holder to report loss or compromise of an authenticator, and can either:
- deregister the authenticator and support a process for reregistration; or
- if appropriate, close the associated account and require reenrolment.
Additional information — Where a biometric factor is used and compromise was not prevented by presentation attack detection, disabling needs to include deregistering as the biometric characteristic cannot be revoked.
Objective 3 — Prevent use of a physically acquired possession factor
Rationale
An authenticator may be compromised by being physically acquired by someone else.
Possession factors can be acquired by another entity as occasional unauthorised usage or permanent theft.
Where a possession factor is a physical item, the authenticator holder can become aware that it has been stolen. Requirements for non-physical challenges on possessions and biometric characteristics are covered under Objective 5.
This control applies where a possession factor is used.
AA3.01 Control
The RP prevents use of a physically acquired possession factor by combining it with an authentication factor of another type.
For level 1 and 2 — This control does not apply. Controls in Objective 2 serve.
For level 3 — The RP MUST undertake this control.
For level 4 — The RP MUST undertake this control using a biometric factor as the second factor.
Additional information — This objective could be met by combining a possession with a knowledge factor. However, the level 4 requirement has been restricted to a biometric factor to be consistent with the need for this combination in other level 4 controls.
Objective 4 — Protect knowledge factor response from being guessed
Rationale
An unauthorised entity can obtain control of a knowledge factor by providing the response that the challenger expects. This threat is most significant when the expected response is static, as once obtained it can be used for multiple authentications. If an expected response is dynamic, then the correct initial response cannot be reused for a subsequent authentication.
Widespread attacks across many authenticators utilise some form of guessing which may follow sequences, patterns, lists such as dictionaries, or similar techniques.
Targeted attacks on a few authenticators may utilise some form of discovery to obtain the possible correct responses such as using a list of previously compromised list secrets or the underlying key used to generate a response.
Limiting the number of unsuccessful attempts within a time period is an effective way of controlling automated guessing attacks.
These controls apply where a knowledge factor is used. The controls for replicating the codes related to non-physical challenges on possession factors are covered under Objective 5.
AA4.01 Control
The RP implements minimum levels of complexity on any knowledge factor response (secret).
For level 1 and 3 — The RP MUST require a minimum complexity of 4 numeric characters or utilise an equivalent level of complexity for responses such as swiping points, matching pictograms, etc.
For level 2 and 4 — The RP MUST require a minimum complexity of:
- 12 characters; or
- 7 characters from at least 3 of the lower case, upper case, numeric and symbol character sets; or
- an equivalent level of complexity for responses such as swiping points, matching pictograms, security questions, etc.
Additional information — Upper limits on characters should be set high enough to encourage the use of memorable phrases.
AA4.02 Control
The RP limits the creation of easily guessable knowledge factor responses by disallowing repetition or patterns and where the authenticator has the form of an online password, apply the following exclusions (as applicable to the character sets being used):
- disallow repetitive or sequential characters
- disallow specific words, for example the identifier (for example, username), name of the service etc.
- disallow singular dictionary words and common character substitutions
- disallow passwords contained in blacklists (usually include overly common combinations and compromised passwords).
For level 1 and 3 — The RP SHOULD undertake this control.
For level 2 and 4 — The RP MUST undertake this control.
Additional information — These controls are best implemented using a strength meter during knowledge factor establishment.
AA4.03 Control
The RP implements maximum limits for unsuccessful attempts and prevents further attempts for a minimum period.
For level 1 — The RP SHOULD limit unsuccessful attempts to 10 and further attempts for 15 minutes minimum.
For level 2 and above — The RP MUST limit unsuccessful attempts to 5 and disallow further attempts for 30 minutes minimum.
Additional information — In some circumstances, it may be reasonable for the RP to rely on the time and effort taken to provide a response — such as entering a PIN code, as a default control against guessing.
AA4.04 Control
The RP prevents use of a guessed knowledge factor by combining it with an authentication factor of another type.
For level 1 and 2 — This control does not apply.
For level 3 — The RP MUST undertake this control.
For level 4 — The RP MUST undertake this control using a biometric factor as the second factor.
Objective 5 — Preventing manipulation of the holder into disclosing the knowledge factor
Rationale
A manipulation attack involves an interaction with the authenticator holder in order to successfully complete the acquisition of a knowledge factor.
The attack may not be noticed by the authenticator holder, such as keyboard logging or a card skimming device. The attack may be some form of observation such as eavesdropping which succeeds if it’s not noticed by the holder.
Alternatively, the attack may be some form of social engineering covering a wide range of techniques such as phishing, hoax support calls and various other scams which succeed if these appear legitimate to the holder.
Because a knowledge factor challenge usually involves providing the same static response, it may be able to be reused many times without the holder being aware of its use by another entity.
At the higher levels of assurance, combining a knowledge factor challenge with a second challenge of a different type mitigates the threat of a knowledge factor being acquired via manipulation. It also mitigates the threat of guessing (Objective 3) at higher levels.
These controls apply where a knowledge factor is used.
AA5.01 Control
The RP prevents use of a disclosed knowledge factor by combining it with an authentication factor of another type.
For level 1 and 2 — This control does not apply. Controls in Objective 2 serve.
For level 3 — The RP MUST undertake this control.
For level 4 — The RP MUST undertake this control using a biometric factor as the second factor.
Additional information — While at level 4 this objective could be met by combining a knowledge factor with a possession factor, it has been restricted to a biometric factor to be consistent with the need for that combination in other level 4 controls.
Objective 6 — Protecting against replication, forgery, or spoofing of possession and biometric factors
Rationale
Authenticators need to be protected against replication, forgery or spoofing by an attacker including the ability to provide the expected static response or 1 or more dynamic responses.
Knowledge-based authenticators have been covered in Objectives 3 and 4.
Threats against possession-based authenticators can take the following forms:
- replication or forgery of documents or devices that must be physically presented for manual or automated challenge
- replication of the codes (static or dynamic) used to respond to non-physical challenges on possession of a document, device or software
- replication of the value that represents existence in a specific location.
The RP needs to ensure that authenticators based on biometric factors are protected against presentation by another entity (spoofing), including the construction of the expected static response, cloning of 1 or more live responses, or the means to produce all expected live responses.
Some level of protection is provided due to the effort required to undertake successful replication or forgery of a possession factor or spoofing of a biometric.
The requirement for two-factor authentication that protects against physical acquisition at higher levels of assurance also mitigates replication of the expected responses to possession factor challenges.
These controls apply where possession and biometric factors are used.
AA6.01 Control
The RP MUST protect against replication or forgery of a physically presented authenticator by incorporating features that ensure the cost of doing so is relative to the level of assurance.
AA6.02 Control
The RP uses dynamic, non-predictable responses to non-physical challenges on possession factors and limits the response validity to a maximum of 10 minutes or 1 minute, where little messaging delay exists.
For level 1 — The RP MAY undertake this control.
For level 2 and above — The RP MUST undertake this control.
Additional information — The limits need to be sufficiently short to reduce malicious reuse and sufficiently long to be useable by the holder. They can be influenced by the holder group (for example, technologically savvy versus challenged) and the type of authenticator (for example, code receiver versus code generator).
AA6.03 Control
The RP MUST, for responses to non-physical challenges on possession factors, utilise a minimum complexity of:
- 6 numeric characters; or
- 4 alphanumeric characters; or
- an equivalent level for other codes such as pictograms.
Additional information — For usability or avoidance of inappropriate words, some alphanumeric characters MAY be restricted when generating the received codes.
AA6.04 Control
The RP addresses spoofing of biometric challenges by ensuring the biometric response is obtained from the person using appropriate measures to detect spoofing attempts (for example, recordings, masks, makeup or prosthetics etc.)
For level 1 — The RP SHOULD undertake this control.
For level 2 and above — The RP MUST undertake this control.
Additional information — This control can also help reduce the occurrence of false acceptance of biometric comparisons when spoofing attempts are successfully recognised.
AA6.05 Control
The RP obtains biometric factor samples in person or remotely incorporating liveness checking which demonstrates at least 90% resistance to presentation attacks.
For level 1 to 3 — This control does not apply.
For level 4 — The RP MUST undertake this control.
Additional information — Current best minimum practice for resistance to presentation attacks using technology is the use of Clause 12 of ISO/IEC 30107-3.
Objective 7 — Managing biometric factor probability
Rationale
Biometric characteristics suitable for authentication are substantively unique to individual entities. Therefore, an authenticator with a biometric factor challenge is potentially a more reliable means of authenticating a specific entity than a knowledge or possession factor. However, unlike the other 2 factor types, a biometric response is probabilistic rather than binary.
There remains the possibility that a manual or systematic comparison will incorrectly match a biometric response from another entity with that of the enrolled entity, resulting in a false positive response to the challenge.
At lower levels of assurance, false positives for a biometric factor challenge should be less than the unmitigated risks for knowledge or possession factor challenges.
There are no additional controls for the lower levels and the RP will need to accept that a small proportion of false positive results may be received.
For higher levels of assurance, an authenticator with a biometric factor needs to have a very low false positive rate and be used in combination with another authentication factor to protect against the statistical possibility of incorrect authentication.
AA7.01 Control
The RP reduces the occurrence of false positives in biometric comparisons by using:
- manual comparison of the biometric characteristic by a trained operator
- systematic comparison with a rate of <0.01% false positives, based on a one-to-one comparison.
For level 1 and 2 — This control does not apply
For level 3 — The RP MUST undertake the control using 1 of the ways stated
For level 4 — The RP MUST use systematic comparison.
Additional information — At level 4 manual comparison may be used, however, it needs to be supported by systematic comparison.
AA7.02 Control
The RP protects against the probabilistic nature of biometric comparisons by combining it with an authentication factor of another type.
For level 1 and 2 — This control does not apply.
For level 3 — The RP MUST undertake this control, when using manual comparison.
For level 4 — The RP MUST undertake this control.
Objective 8 — Authentication event can be investigated
Rationale
An important element of trust in any identification process is the ability for an Entity or Relying Party to question a process or presentation.
AA8.01 Control
The RP MUST store appropriate detail about an authentication event to enable queries or investigation in the future.
What compliance means
These requirements are provided as good practice for any RP wishing to contribute to the prevention of identity theft and fraud.
Compliance with this standard will be given through means such as contractual requirements, cabinet mandate, legislation etc., which will include mechanisms for assessment and certification.
In order to comply with this standard, an RP needs to meet all the applicable controls for the selected level of authentication assurance.
Applicable controls are determined by the authentication factor(s) used in the authenticator.
In general:
- LoAA1 can be achieved using a single factor authenticator with few controls
- LoAA2 using a single factor authenticator with some additional controls
- LoAA3 using a good biometric factor or combining 2 different factor types in the authenticator
- LoAA4 using 2 different factor types where 1 is a biometric factor implemented with liveness checking.
Related advice
If the RP is providing authentication assurance services to other parties, there will be additional controls to be applied in the Federation Assurance Standard.
A companion implementation guide will be developed for this standard and published in Identification Management — Guidance.
Contact
Te Tari Taiwhenua Department of Internal Affairs
Email: identity@dia.govt.nz
Utility links and page information
Last updated

